 As you may know by now, Facebook announced a massive data breach today affecting at least 50 million (yup you read that right) users.
As you may know by now, Facebook announced a massive data breach today affecting at least 50 million (yup you read that right) users.
It seems that a vulnerability in Facebook’s code for the “ViewAs” feature was exploited allowing the attackers to compromise access tokens which are digital unique identifiers of you and your account and prevents you from having to re-enter your password multiple times which would drive you crazy if you had to.
Facebook states that “there’s no need for anyone to change their passwords” however are you willing to trust your privacy to Facebook? Can those two words even be in the same sentence? Probably not. Be proactive and change your password which will regenerate the access tokens associated to your account assuring your account is safe.
It seems like the vulnerability has been there since July of 2017 and was just recently identified and corrected. So this “leak” has been there for a while.
Here are several links with more technical details on the Facebook breach, should you be interested:
So the reality is Facebook and most reputable technology firms go to great legnths to get coding right and keep it secure but it is not uncommon that future modifications of existing code cause changes and vulnerabilities not perceived by the developer making the change. Organizations that have developers working with this kind of code typically have Change Management in place which primary purpose is understanding what effect a change in older code will make. Honestly, it is impossible to cover all scenarios but exposing 50 Million customers private data is not acceptable!
In today’s environment of constant data breaches and privacy compromises you shouldn’t be surprised but at the same time, you should become numb to this issue and protecting your privacy and data should stay high on your priority list. However, it will not protect itself and it has become painfully obvious you can’t rely on the “big players’ either. Be proactive!
What Can I Do Besides Change My Password?
Use Common Sense – First and foremost (and I’m sure you’ve heard if before) common sense should be in play. Be extremely cautious of what you post to social media. Yeah its great to share pics with friends and other interesting items but telling everyone in the world you are on vacation in another country (and that your home is currently empty) is probably not the smartest thing to do. Posting pics is great but consider whats in the picture frame before you take the shot. Are your vehicle tags in the frame? It is way too common to see pics posted on social media that contain things allowing someone to determine locations and identities. Facebook’s face recognition should scare you all by itself and especially your kids.Think ahead.
Use 2-Factor Authentication (also known as 2FA) – 2FA is where you have set up to send an authentication code to mobile devices verifying you are the owner of an account or password. Sure it can be a pain in the butt if you don’t have your phone with you but there are usually ways to do 2FA without your phone. This prevents unauthorized access to your accounts should your password be compromised. Use 2FA when possible!
Use Private Browsing – While certainly not full proof using your browser “private browsing” function, which is not on by default, helps protect the data stream between your computer and the websites you visit.
Use Complex Password – It baffles us how often we see 5-letter super simple passwords that are super simple to compromise. Start using sentences as passwords instead of one word. Most systems limit the minimum number of characters but not the maximum. Recently had a customer whose passwords were her pets name and her account was recently compromised. She couldn’t figure out what happened until we showed her the pics she posted all over Facebook of the pet WITH the pet’s name. Social engineering at its best! Also, we find customers using sentences as passwords are less likely to forget them which is a bonus.
How Do I Keep Up With All These Passwords? – Well, the answer certainly isn’t having everything with the same password! You are making it too easy to compromise. If you find you have too many passwords to track, use a password manager. Not only will it store and auto-enter your passwords, but you can also let it generate a complex password that you don’t have to recall. We highly recommend #LastPass. Shring has done very intensive testing of various password managers and LastPass is the winner. Check it out here.






 No one likes passwords. Creating them. Remembering them. Typing them in.
No one likes passwords. Creating them. Remembering them. Typing them in.
 We have all seen a LOT of change over the past couple of years. You’ve changed the way your business operates, including how we interact with others.
We have all seen a LOT of change over the past couple of years. You’ve changed the way your business operates, including how we interact with others.

 A new report has discovered that 67% of remote workers are using faulty tech when they are working remotely. Often that’s because they’ve accidentally damaged the tech themselves they don’t want to admit it to their boss in case they get into trouble.
A new report has discovered that 67% of remote workers are using faulty tech when they are working remotely. Often that’s because they’ve accidentally damaged the tech themselves they don’t want to admit it to their boss in case they get into trouble.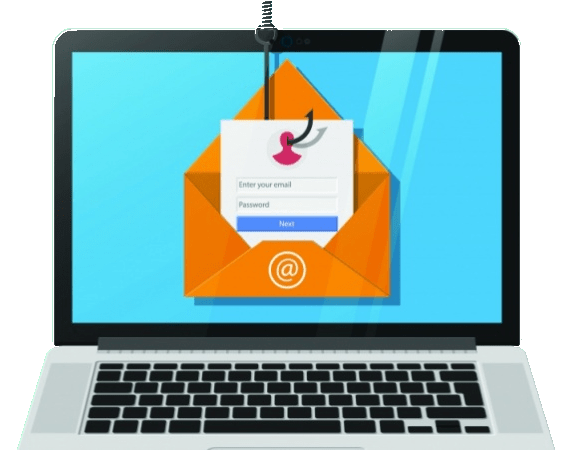
 Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information — such as credit card numbers, bank information, or passwords — on websites that pretend to be legitimate. Cybercriminals typically pretend to be reputable companies, friends, or acquaintances in a fake message, which contains a link to a phishing website.
Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information — such as credit card numbers, bank information, or passwords — on websites that pretend to be legitimate. Cybercriminals typically pretend to be reputable companies, friends, or acquaintances in a fake message, which contains a link to a phishing website.