Who is protecting your business?
 There are many potential threats to you personally, your organization, and its mission-critical data.
There are many potential threats to you personally, your organization, and its mission-critical data.
It’s become easy to be numb to the constant barrage of threats focused on us and our businesses. We can help!
Running a single piece of software on your workstation is no longer anywhere close enough to provide any real protection and honestly … it’s foolish to think so.
Unified Threat Management – A New Approach
As a multi-service platform, Unified Threat Management (UTM) incorporates the broadest level of protection available. UTM also combines multiple security features into a single platform, protecting against attacks, viruses, trojans, spyware, and other malicious threats. Incorporating Deep Packet Inspection and gateway protection allows us to deliver superior performance at a reasonable price. Unified Threat Management brings you the best of both worlds—reducing complexity and simplifying management while delivering multiple layers of protection under a single management console.
Our Unified Threat Management Framework
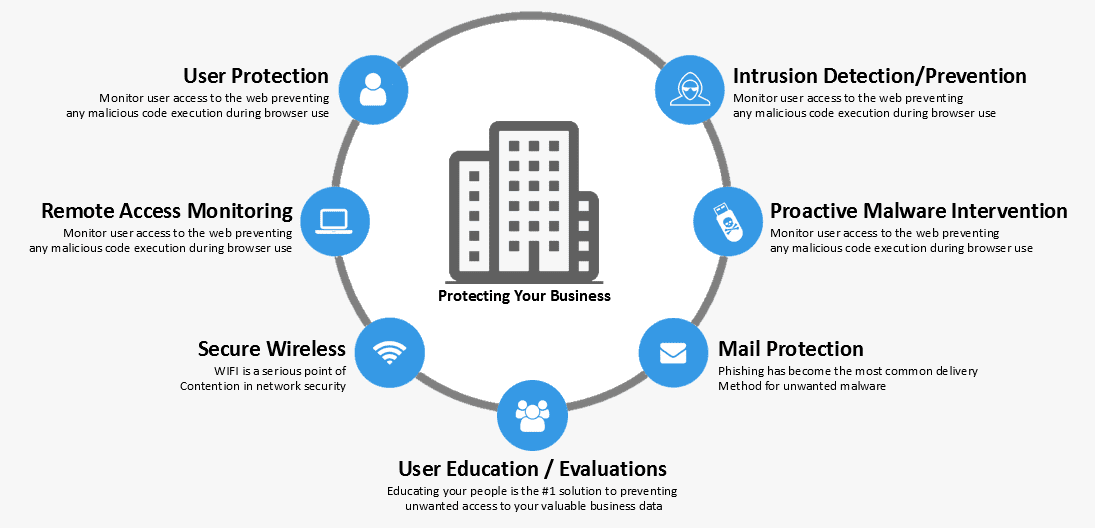
Unified Threat Management has become very popular, and several security companies have adopted this approach. However, many of them require file caching and rebooting during the file scan and update processes, and this causes serious performance and availability problems. We do not utilize file caching or restarting and, in fact, we provide the only solution on the market that can handle unlimited file sizes and six thousand concurrent downloads. Our solutions are capable of handling even the fastest-growing network with superior scalability and performance.
3 Key Approaches To Protecting Your Business
-
TECHNOLOGY
- Threat Management tech is great and constantly adapting but tech-alone will not protect your business and data!.
-
EDUCATION
- Educating your staff should be the number one focus in regards to threat prevention.
-
MONITORING
- Proactive Monitoring and Response is the final piece for a secure infrastructure.
